
Ultimate Guide to NIST Security Standards – All You Need to Know About the Cybersecurity Guidelines
Running a business nowadays requires a lot of things, especially those regarding the Internet and technology.
Although such things facilitate the business in many ways, they can also be a source of many threats that could affect your privacy and jeopardize your entire company’s safety or put your sensitive files at risk of the powerful cyberattacks.
Therefore, all the private sector organizations and businesses in the United States should have the NIST compliance, which provides guidance on how to assess and improve the ability to detect, prevent, and respond to the most advanced forms of cyberattacks.
What is NIST?
The National Institute of Standards and Technology (NIST) is an agency within the US Department of Commerce, which creates standards in the science and tech industries.
These standards are included in NIST guidelines, which provide recommended security controls for information systems at federal organizations that assess security risks.
That said, all those companies comply with NIST standards because they include the best practices regarding cybersecurity and guide you through the essential process of protecting your data.

What is NIST Compliance?
When you say that you’re NIST compliant, that means that you agree with the password guidelines set by NIST.
NIST guidelines offer advice on how users should approach password security and complexity, and they are used by many federal institutions, agencies, businesses, and universities for more than ten years.
Who Needs to Comply With NIST Security Standards?
Even though NIST standards are primarily designed for federal organizations and businesses, any company that collaborates with the government should be NIST compliant, for example:
- Government staffing agencies
- Procurement services providers
- Manufacturers that sell products to the government
- Manufacturers that sell to government suppliers
- Higher learning institutions, including universities
- Research institutions
- Consulting companies
- Service providers
All these companies and institutions need to comply with the NIST regulations because they contain sensitive information that belongs to their clients, customers, employees, students, etc., and such data needs to be secure and safe.
Apart from meeting industry and governmental regulations, NIST standards will help to protect sensitive infrastructure from insider threats and attacks that come from outside. Besides, it helps your IT team protect the network from malware, ransomware, and other sophisticated cyberattacks.
All the companies that want to collaborate with the Department of Defense, NASA, the Department of Transportation, and others are obliged to provide security standards that meet at least those listed in NIST 800-171, but since hackers have developed their strategies, organizations will need to have security protocols and procedures that go beyond NIST standards.
What is the Difference Between NIST 800 and NIST 800-171?
When exploring the concept of NIST, you must see the frequent mentions of NIST 800 and NIST 800-171 – and you must be wondering what they refer to?

Both designations are related to NIST series that include different security requirements – NIST 800 series is a set of documents that describe the US federal government computer security policies that optimize the protection of IT systems and networks, and they are available for free.
On the other hand, NIST 800-171 compliance includes secure file sharing and information exchange, and they relate to how you store, access, exchange, and govern sensitive but unclassified information with the agency.

As mentioned in the previous section, all the non-federal agencies that do business with government and the Department of Defense (DOD) must be NIST 800-171 compliant, and you must understand specific parameters and technical terms to achieve such compliance.
NIST 800-171 categorizes sensitive (controlled) information into two groups, which are technical and unclassified.
Controlled technical information (CTI) refers to military or space applications, while Controlled unclassified information (CUI) is more common and includes the data about patents, finances, court records, and any other type of information that must be private but doesn’t require a high-level security clearance to view.
All the contractors must use covered information systems, which include email, FTP (File Transfer Protocol), enterprise content management, on-premise, and cloud-based storage systems, file sharing, and collaboration platforms, as well as employee endpoints such as laptops, tablets, and smartphones.
All the mentioned systems are owned or operated by a contractor that processes, stores, or transmits Federal contract information, which needs to be covered with the latest security protocols.
Therefore, all the companies that collaborate with the Department of Defense must follow the terms of secure file sharing and information exchange policies to safely transmit sensitive information, such as credit card number, web and electronic mail services, processing healthcare data, providing cloud services, and developing communications, satellite, and weapons systems.
When it comes to protecting your CUI, consider this ultimate NIST 800-171 checklist of 7 steps on how to keep your unclassified information entirely safe:
- Locate the CUI: The first thing you should do is to identify the systems in your network that contain CUI. Such systems could be CIFS (Common Internet File System) files, SharePoint, cloud storage (OneDrive for Business and Box), endpoints, and portable hard drives.
- Categorize the Information: It’s essential to classify the files that fall under the category of CUI and separate them from other data that do not qualify. This will enhance the process of demonstrating NIST compliance when performing the audit.
- Set limitations: Make sure you give access to authorized employees so that they are the only ones who can download and share files that contain CUI. Also, don’t forget to set the expiration dates to files or folder that contain CUI since you can prevent access after the project’s been completed.
- Implement encryption: You can add an extra layer of security by encrypting all the systems that hold or transmit your data. This will enable compliance and won’t affect authorized users’ ability to share files using email, FTP, and other services.
- Monitor the activities: Make sure you know who has access to CUI and how they’re using it. According to 800-171 compliance, all the contractors must ensure the actions of their employees are regularly traced, no matter if they’re malicious or not. Besides, regular monitoring can detect any potential anomalies.
- Train the employees: Educate your employees on the basics about information exchange, make sure they’re aware of the security risks that come together with CUI, and teach them how to identify suspicious emails and insider threats that could allow an unauthorized source to access and download the CUI.
- Assess: It’s vital to conduct a security assessment that inspects all systems, environments, and information exchange procedures to assess risks.
What are the Most Common NIST Security Standards?
Several NIST standards are used in everyday security evaluations, and the most common ones are:
NIST Cybersecurity Framework
The NIST Cybersecurity Framework is also known as a NIST risk management framework, and it is based on existing standards, guidelines, and practices. It is voluntary guidance, and it’s aimed at critical infrastructure organizations to manage better and reduce cybersecurity risk.
It doesn’t provide new technologies, standards, or concepts, but it instead integrates cybersecurity practices developed by organizations such as NIST.
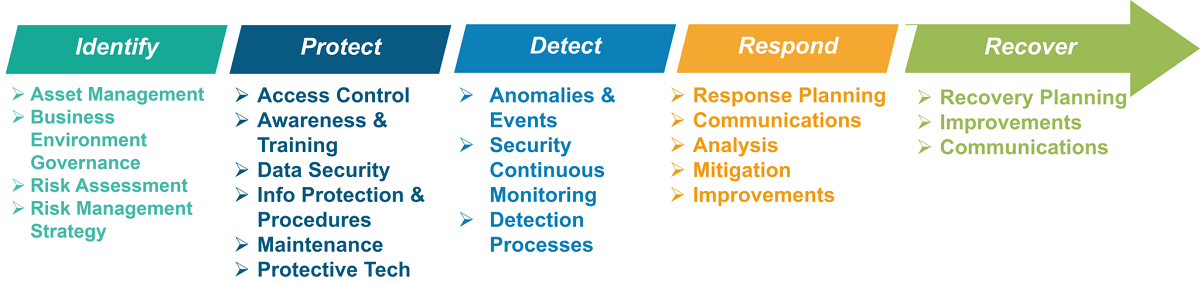
Identify
The first function is aimed at developing the organizational understanding to manage cybersecurity risks to systems, assets, data, and capabilities. It is present in the following categories:
- Asset Management (ID.AM): This refers to the data, personnel, devices, systems, and facilities that allow the organization to achieve business purposes. They are considered to have relative importance to business goals and their risk strategy.
- Business Environment (ID.BE): This is the group of the organization’s mission, objectives, stakeholders, and other activities that are considered prioritized. Such information is used to inform cybersecurity roles, responsibilities, and risk management decisions.
- Governance (ID.GV): These are policies, procedures, and processes that manage and monitor the institution’s regulatory, legal, risk, environmental, and operational requirements.
- Risk Assessment (ID.RA): This means that the organization understands the cybersecurity risk to organizational operations, including mission, functions, image, or reputation, as well as corporate assets and individuals.
- Risk Management Strategy (ID.RM): This includes the priorities, constraints, risk tolerances, and assumptions within the company, which are established and used to support operational risk decisions.
Protect
To protect means to develop and implement the appropriate safeguards to provide delivery of vital infrastructure services, and it includes:
- Access Control (PR.AC): The access to sensitive assets and associated facilities is limited to authorized users, processes, or devices, as well as to permitted activities and transactions.
- Awareness and Training (PR.AT): The personnel and partners within the organization are provided with cybersecurity awareness education and are trained to perform their security-related duties and responsibilities according to related policies, procedures, and agreements.
- Data Security (PR.DS): All the information and data are managed under the organization’s risk strategy to protect the integrity, availability, and confidentiality of the information.
- Information Protection Processes and Procedures (PR.IP): All the security policies, processes, and procedures are maintained and used to manage the protection of information systems and assets.
- Maintenance (PR.MA): Maintenance and repairs of industrial control and information system components are always performed in line with policies and procedures.
- Protective Technology (PR.PT): All the technical security solutions are managed to ensure the security and resilience of systems and assets according to policies, procedures, and agreements.
Detect
Detection encompasses the development and implementation of adequate activities in order to identify the occurrence of a cybersecurity event – it includes:
- Anomalies and Events (DE.AE): All the anomalous and malicious activities are detected on time, and the potential impact of events is entirely understood.
- Security Continuous Monitoring (DE.CM): The entire information system and assets are discretely monitored so that all the cybersecurity events can be identified. Also, the efficiency of proactive measures should be verified.
- Detection Processes (DE.DP): The detection processes and other procedures are maintained and tested to make sure there are set timely and adequate awareness of unusual events.
Respond
When it comes to responding function, we should say that it develops and implements the appropriate activities intending to take action regarding a detected cybersecurity matter. It refers to the next categories:
- Response Planning (RS.RP): The processes and procedures regarding response planning are executed and maintained to provide timely response to detected events associated with cybersecurity.
- Communications (RS.CO): Communications refer to response activities that are coordinated with internal and external stakeholders so that they include external support from law enforcement agencies.
- Analysis (RS.AN): Analysis is made to ensure adequate response and support all the recovery activities.
- Mitigation (RS.MI): All the activities are performed to prevent the expansion of malicious activity, mitigate its effects, and eliminate the incident.
- Improvements (RS.IM): The activities regarding organizational response activities are improved by incorporating lessons learned from previous detection/response activities.
Recover
Recovery is in this case associated with the development and implementation of the activities that maintain plans for resilience and restore any capabilities or services that were impaired due to a cybersecurity event:
- Recovery Planning (RC.RP): All the recovery processes and procedures are executed and maintained to provide timely restoration of systems or assets that are affected by a cybersecurity event.
- Improvements (RC.IM): The whole process of recovery planning is improved by implementing the learned lessons to future activities.
- Communications (RC.CO): All the restoration activities are coordinated with internal and external parties, including coordinating centers, Internet Service Providers (ISPs), attacking system owners, victims, other CSIRTSs (Computer Security Incident Response Team), and vendors.
Federal Information Processing Standards (FIPS)
Federal Information Processing Standards are used as guidelines for processing and handling the documents. All the government agencies, contractors, and vendors use these standards to manage data and encryption algorithms, and they are mandatory for all the computers used within the government.
Besides, all the organizations that interact with data protected by these rules, including contractors and subcontractors, must ensure compliance following NIST security standards and guidelines.
Although FIPS is primarily designed for federal purposes, many companies in the private sectors voluntarily use these standards, and the following list includes the most common ones:
- Security Requirements for Cryptographic Modules
- Secure Hash Standard
- Digital Signature Standard
- The Keyed-Hash Message Authentication Code (HMAC)
- Standards for Security Categorization of Federal Information and Information Systems
- Minimum Security Requirements for Federal Information and Information Systems
- Personal Identity Verification (PIV) of Federal Employees and Contractors
- SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions
You should know that not all of the FIPS standards are applicable and mandatory for Federal agencies, and they do not apply to national security systems.
Internal and External Audits
Internal and external audits are essential because they help organizations identify weaknesses in data handling, security, and regulatory compliance. They can help reduce the risk and avoid potential fines or legal issues for noncompliance since they make sure businesses maintain the strict protocols vital for protecting assets.
An organization’s staff primarily initiates internal audits to assess risk, compliance, and security, and its management can be quite complex. Internal audits should be performed regularly so that they demonstrate a commitment to protect data proactively.
External audits, on the other hand, are more formal, and third-party companies often handle them. These audits will check for compliance against particular federal, state, industry, and corporate rules and standards.
NIST Password Standards
NIST password standards are designated as NIST 800-63 Password Guidelines, and they refer to password complexity and its frequent change.

Since many cyberattacks arise due to weak and reused passwords, NIST published its 74-page paper on Digital Identity Guidelines, where they recommend the passwords that should be “easy to remember and hard to guess,” which is a counter to the former opinions that passwords need to be long and complex.
In a nutshell, the NIST password guidelines recommend the following password specifications:
- A minimum of eight, and a maximum of at least 64 characters
- The ability to use all the special characters if possible
- Avoid sequential and repetitive characters such as 123456 or aaaaa
- Avoid context-specific passwords that include the name of the site, or similar
- Avoid commonly used passwords (p@ssw0rd, and similar) and dictionary words
- Avoid passwords that come from previous breach corpuses
- Avoid password hints
- No knowledge-based authentication (What’s the name of your first pet?)
As you can see, there is no need for password complexity, but it’s recommended to avoid predictability that’s the most common reason for breaches. If you can’t remember your current passwords, use a password manager app that can securely save all of them, making sure you are the only one who can access your critical files.
How to Become NIST-Certified?
The government doesn’t offer an official NIST certification program, but the vendors should certify their company by themselves, and make sure it’s meeting the required NIST requirements.
Businesses of all sizes need to go through a formal Certification and Accreditation process, which helps ensure the security of information systems by measuring and minimizing the potential risk.
Certification includes the process of examining, evaluating, and testing security controls that have been already based on the type of information system, while the accreditation encompasses the process of formally accepting the risks that are present in the system since it’s not possible to remove all the risk.
However, if your company fails to take the necessary steps to maintain compliance, you can face severe fines or even fraud charges that come as a consequence of breaking the rules of the contract.
Also, if you are a subcontractor who doesn’t meet the standards of NIST compliance, you will be excluded from the project you’re working on or removed from the list of approved vendors.
Secure Networks Helps You Understand the NIST Compliance Better
Although NIST compliance helps you identify the most sensitive areas and prioritize your protection, it doesn’t guarantee that your data will remain secure.
Your organization needs assistance from the professional IT service provider, such as Secure Networks ITC, who’ll help you elevate your standards and maintain the best practices in a safe cyber environment.
Our goal is to help you understand the importance of NIST regulations, to provide assessment, consulting, and implementation of services to meet NIST requirements. Request NIST assessment today and learn more about our fast and efficient IT support.

