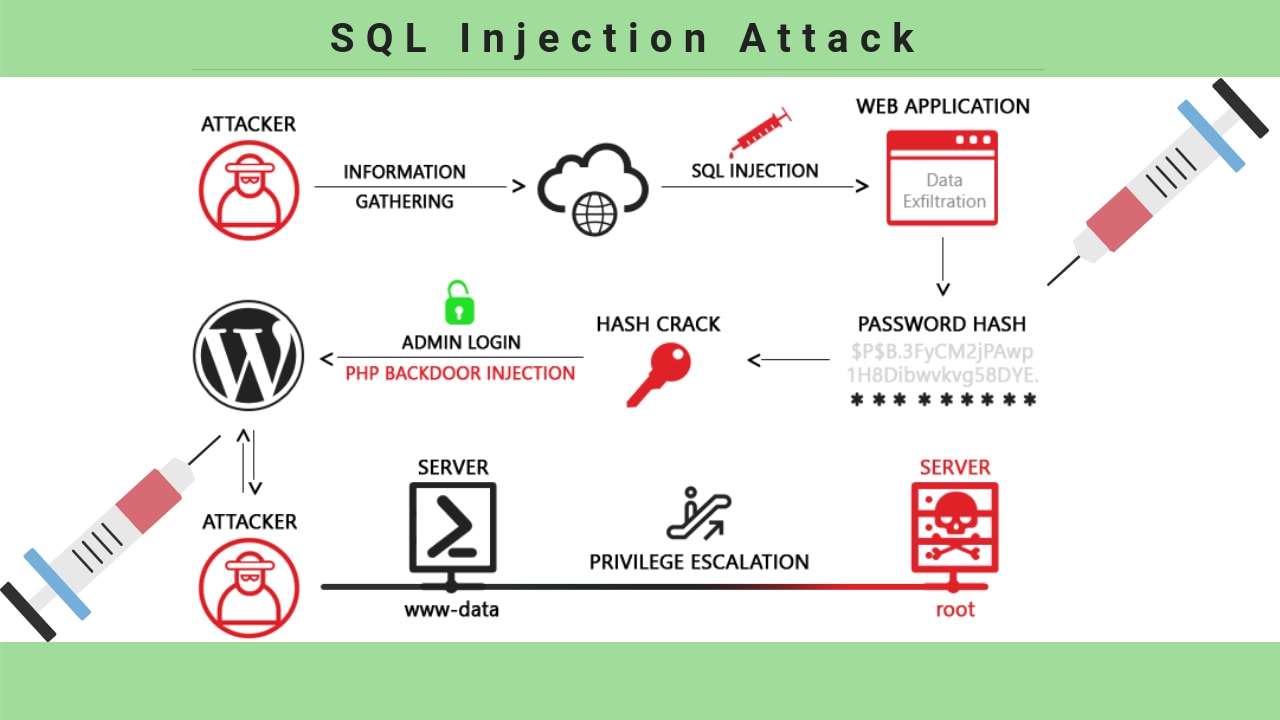
SQL Injection Attack - ”Open Your Eyes”
In December of 1998 the well-known hacker Jeff Foristal alias Rain Forrest Puppy was writing about how to hack a Windows NT server. He discovers one of the first SQL attacks in the history. In the late 1990s, just a few websites were using full Microsoft SQL server databases. Admins prefer to use simple Microsoft Access-based databases. That's why was so easy to attack and exploit databases and servers. Even after almost twenty years, SQL injection still is a significant security issue. SQL injection is discovered more than 20 years ago and remains all these years as the potent malicious cyber-attack and require top database security priority. It was applied in the run-up to the 2016 U.S. presidential election to use the personal data of about 200,000 Illinois voters, and in high-profile attacks against corporations and establishments like a PBS, Sony, Yahoo, Microsoft, Heartland Payment Systems, and the CIA also. Structured Query Language (SQL), is the control and command language for relational databases like a MySQL, Microsoft SQL Server, and Oracle. In present-day web development, databases have frequently used in the back end of web apps and content management systems composed in PHP, ASP.NET or different scripting languages. This means that the content and behavior of websites rely on a database server. A lucrative attack on the database that launches a web app or a website, like an SQL login bypass attack, can provide a culprit a wide range of powers, from defacing (altering website content) to capturing sensitive information like the personal account data or private business information. An SQL commands list is the identical like a database commands list, such as possibly the most dangerous one a “drop table."What is SQL Injection?
SQL injection, also called SQLi, is an attack that uses malicious SQL code for back-end database manipulation to gain info that wasn’t meant to be exposed. This info may include contact forms, sensitive company data, shopping carts, support request or private client information. The effect that SQLi can have on an organization or business is devastating. A lucrative attempt may outcome in the sensitive customer data, intellectual property or personal details (phone numbers, addresses, credit card details). SQLi can attack any database, but websites are the most common targets.
Types of SQLi Injection

SQLi can be used in a numerous different way to produce severe issues. By using a SQL injection, the culprit might skip authentication, access, alter and delete data inside of the database. In some circumstances, SQLi could be used to run commands on the operating system, possibly enabling a fraudster to expand with more malicious attacks within a network that is on firewall backside.
SQLi has 3 main types:
• In-band SQLi
• Inferential (Blind) SQLi
• Out-of-band SQLi.
In-band SQLi
In-band SQL Injection (Classic SQLi) is the most typical type of SQL injection attacks. It occurs when a cyber-criminal is in the position to exploit the same communication channel to both launch attack and collect results. The 2 most typical types of classic SQLI are error-based SQLi and union-based SQLi. Error-based SQLi Error-based SQLi is a classic SQLi method that depends on error message sent by a database server to gather info about the structure of the database. In certain circumstances, this technique alone is competent for a fraudster to enumerate a complete database. Although errors are very helpful throughout the development stage of a web app, they must be disabled on a live website or logged to a file with limited access as a second option. Union-based SQLi Union-based SQLI is a classic SQLi method that uses the union SQL operator to integrate results of 2 or more selected statements into a single one which has then turned back as a HTTP response part.Blind (Inferential) SQLi
Blind SQLi, in contrary on classic SQLi, means that an attacker needs more time to exploit. Still, it is malicious as any other type of SQLi attacks. In this inferential form of SQL injection, no data has indeed sent by the web app, and the perpetrator wouldn't identify the result of an attack. Preferably, a culprit is capable of rebuilding the database structure by transferring payloads, monitoring the web app’s response and the resulting act of the database server. The 2 main types of Blind SQLI are blind-boolean-based SQLi and blind-time-based SQLi. Blind-Boolean-Based SQLi Boolean-based (content-based) SQLi is an interferential SQLi method that depends on sending a SQL query to the database which causes on a database to wait for a particular time (in seconds) before responding. The respond duration will signal to the fraudster either the query result is true or false. Relying on the query result, an HTTP response will be returned with a timeout or instantly. It makes a cyber-criminal being able to conclude if the payload used returned as false or true, although no data from a database was returned. A time-based attack is slow because the perpetrator needs to enumerate the entire database.Out-of-Band SQLi
It’s not very often SQLi injection, generally, since it relies on enabling functions on the database server, that's used by the web app. Out-of-band SQLi appears when a fraudster isn't able to use the same channel to run the attack and obtain results. These methods, provide cyber-criminal an option from interferential time-based solutions, mainly if the server responses aren't very reliable. Out-of-band SQL injection solutions would depend on the database server's capability to create DNS or HTTP requests to transfer data to a fraudster. Here is the one SQL injection attack example, the Microsoft SQL servers xp_delete_file command, which can be applied to create DNS requests to a server as a culprit’s controls.How to Prevent SQL Injection
The great news is that there're a lot of solutions that sites and web apps owners can do to prevent an SQLi attack. Even though there isn't a guarantee and 100% solution in network security, you must prepare and educate yourself. Here're 10 tips how you can minimize the risk of being a target to an SQLi attack.- Be cautious: Suppose, all user-submit info can wide open doors to the attack, so apply input validation by a feature as MySQL’s mysql_real_escape_string () to make sure that any malicious characters haven't passed to a SQL query through data. You must sanitize each data by filtering user data by context. For instance, email addresses must be filtered to enable only the characters allowed in email addresses or cell phone numbers must be filtered to allow for only the digits enabled in a phone number and so forth.
- Avoid dynamic SQL: Frequently, the data sanitization techniques could fail, so apply prepared statements, stored procedures or parameterized queries whenever you can. But, consider the fact that while stored procedures restrict some SQLi types, they slip to guard vs. many others, so don’t depend only on their use for your protection.
- Patch and update: Vulnerabilities in databases and apps that fraudsters can take advantage of have commonly identified, so it's crucial to use patches and updates whenever possible.
- WAF (web application firewall): WAF whether softer or appliance-based is an excellent solution to filter out malicious data. A firewall can be especially useful to serve some security protection versus a new vulnerability before a patch is available.
- Limit your attack surface: Remove any database services that you don't use to prevent attacker leverage off it. For instance, the xp_cmdshell extended stored procedure in MS SQL produces a Windows command shell and make through in a string for execution, which may be very helpful for a fraudster. The Windows operation produced by xp_cmdshell provides the similar security privileges such as the SQL Server service account.
- Apply sufficient privileges: Avoid connecting your database through an account with admin-level privileges except you have some strong reason. Using a restricted account is a safer option, and can reduce an attacker malicious executes. Lead by example, the code behind the login page must query the database using an account restricted exclusively to the relevant credentials table. With this approach, a passage through this channel can’t be used to damage the complete database.
- Limited error message: Attackers obtain themselves with the data about database architecture from error messages, so make sure that they provide minimal info. Apply the (RemoteOnly) custom errors mode or similar wordy error messages on the local computer and at the same time, and make sure that the fraudsters get only the unhandled error message.
- Permanently maintain SQL statements from database-connected apps: This will provide to detect fake SQL vulnerabilities and comments. Supervising tools that exploit computer learning or behavioral analyses can be beneficial.
- Use adequate softer: Your code writers must be responsible for checking the code and for fixing security gaps in a custom app before the software installed.

