DoS and DDoS Attacks - "They Shall Not Pass"
The former director of the F.B.I., Robert Mueller once said, “There are only two types of companies: those that have been hacked and those that will be.” By some rough calculation, 90% of US companies have been hacked. State agencies, such as the N.S.A. and the Department of Homeland Security are in charge of defending state networks. But, the private companies are left alone to protect themselves from the attacks of the DoS and his “more dangerous malware kid” DDoS. The battle between cyber-crooks and government has been going on for decades. These rows will help you to understand what is DoS/DDoS, types of attacks, how to prevent their strikes, and how to educate yourself properly to protect your network and business from malware attacks.What is a DoS Attack?
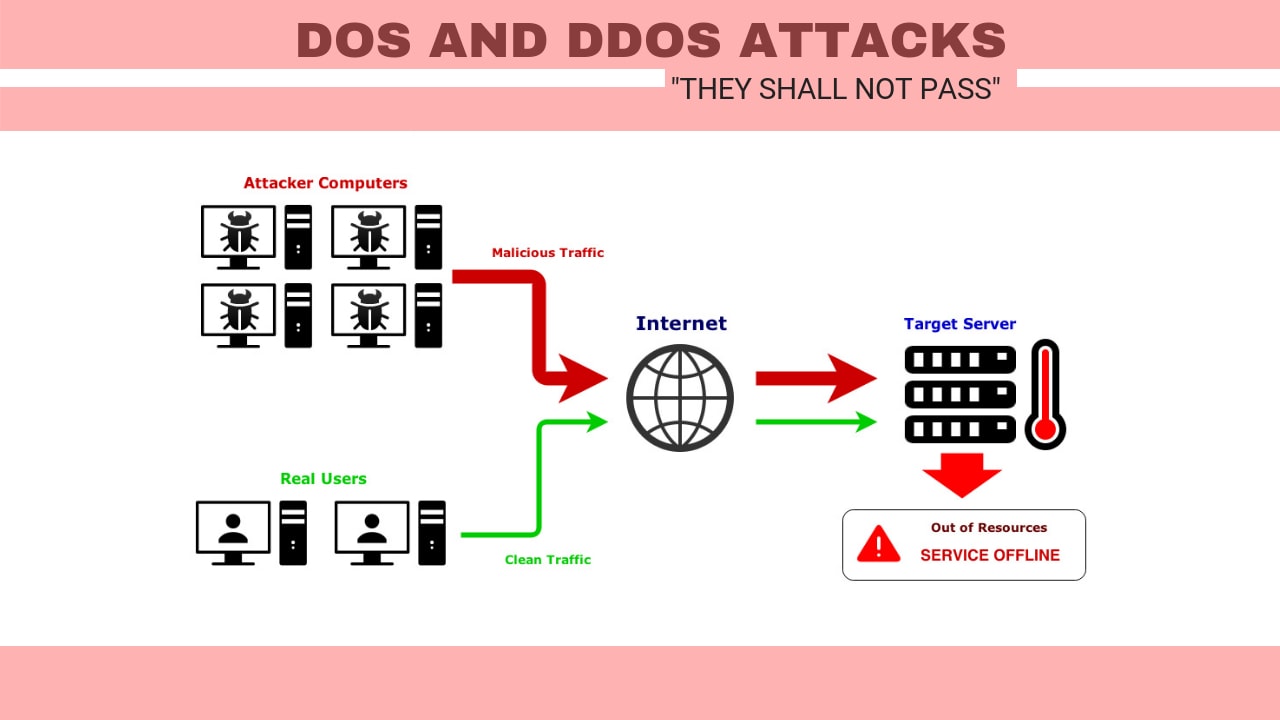
A denial-of-service (DoS attack) is an attempt when legit users aren’t able to approach information systems, devices, or other network resources because of the action by malicious cyber-criminals. Affected services may contain email, websites, banking accounts or other services that depend on the influenced network on the computer. A denial-of-service is realized by overflowing the targeted host or network with traffic until the target can't respond or crashes, blocking the legit user's access. These attacks can cost a person or company both money and time, while their services and resources are unavailable.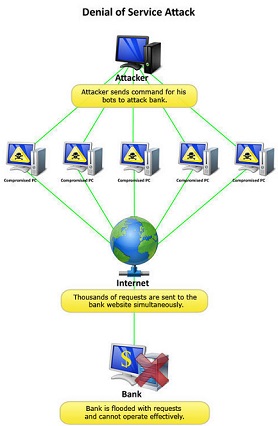
What is DDoS Attack?
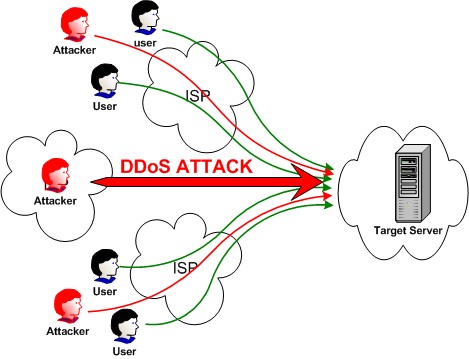
A distributed denial-of-service (DDoS) attacks happen when multiple devices are running together to attack 1 target. DDoS permits for exponentially more request to be sent to the destination, consequently boosting the attack power. It also highlights the attribution difficulty, so the leading source of an attack is harder to locate and find. DDoS strikers frequently applied the use of a botnet (a group of hijacked internet-connected devices to perform numerous attacks). The strikers capitalize on the safety permeability or device weakness to take over control a range-scale of devices using command and control software. Once, it takes power, a cyber-criminal can direct their botnet to lead DDoS on target.
DDoS attacks get higher to a significant degree as devices increasingly come online via the IoT (Internet of Things). IoT devices usually use default pass and don't contain sound security posters, making them an easy target for malware attacks. An affectation for Iot devices frequently goes unnoticed by users, and threat actor could efficiently compromise a hundred or thousand devices to perform a high-scale strike without the knowledge of device owners.
Types of DoS Attacks
Here is the list of 5 major DoS attacks: 1. Syn Flood: Is a type of DoS attack in which hackers compromise multiple devices and synchronously floods the target with numerous SYN packets. The target will be saturated by the SYN requests, causing it to crash, or its performance has decreased severely. 2. IP Fragmentation Attacks: These are an attack that struggles vs. reassembling capability of the target. Numberless fragmented packages are sent to the target, causing it difficulty for the target to reassemble them and result in denying access to the validate users.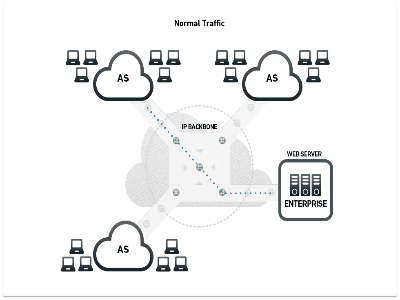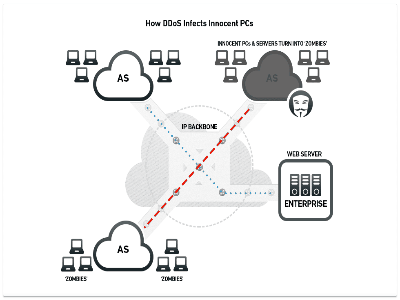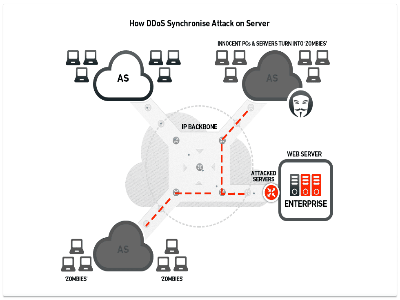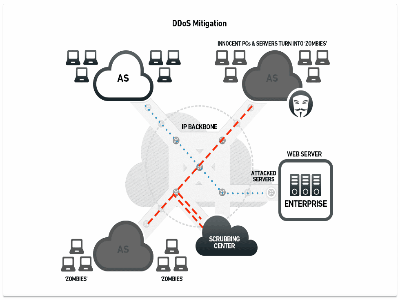
DDoS Attack :Source
3. State Exhaustion (TCP) Attack: The attacker starts and tears down TCP connections and takes control of the stable tables, producing a DoS attack. 4. Application Layer Attacks: The perpetrator uses the programming errors in the device to creates the denial of service attack. It has accomplished by sending multiple application requests to the target to disable the target’s resources, so it won’t be capable of servicing any validated clients. 5. Plashing: This is performing by producing permanent damage to the system hardware by sending phony updates to the device, causing them to be absolutely 100% unusable. The best option is to re-install the hardware drivers.
DDoS Types of Attacks
Here is the list of the 10 most common DDoS attacks: 1. UDP Flood: In this attack, the culprit uses UDP datagram–containing IP packages to flood random ports on a victimized network. The targeted system tries to respond to each datagram with an application, but crashes. The system quickly gets overwhelmed as it attempts to process the UDP package reply volume. 2. DNS Flood: Like the UDP flood, this attack includes attackers using numerous amounts of UDP packages to overwhelm server-side resources. But, in this case, the victim is DNS servers and their cache system, with the ambition being to stop the redirection of legit incoming requests to DNS zone resources. 3. HTTP Flood: This strike applies a quite significant number of HTTP GET or POST requests, at first glance legit, to target an application or web server.These requests are usually created to escape detection of the attacker, who gets useful information about a victim before the attack. 4. Ping Flood: It is a common flood type attack that uses a random number of ICMP echo requests, or pings, to overwhelm the target’s network. For every ping sent, a complementary one including the same number of packages is assumed to return. The victim’s system tries to respond to the countless requests, possibly blocking its network bandwidth. 5. DNS Amplification: In this type of attack, a fraudster begins with small queries that use the spoofed IP address of the destined target. Taking advantage of vulnerabilities on publicly-accessible domain name system (DNS) servers, the replies raise up into much bigger UDP package payloads and overload the victim’s servers. 6. SNMP Reflection: The simple network management protocol (SNMP) allows sysadmins to set up remotely and pull data from connected network devices. Using a target’s forged IP address, a hacker can blast many SNMP requests to devices, each being expected to respond in turn. The number of linked devices gets more and more requests, with the network sooner or later being restricted by the amount of SNMP responses. 7. Ping of Death: PoD is a system by which attackers send atypical or stuffed packages (by way of pinging) to block, weaken or crash a victim’s network or service. Memory overload happens when it attempts to rebuild oversized data packages. 8. Fork Bomb: This DoS attack derives from a victim server inside. In an environment based on Unix, a fork method call copies an existing “parent” operation to a “child” operation. Both operations can then run the tasks synchronous in the system kernel independent of one another. With a fork bomb, a fraudster sends so many repetitive forks making the victim’s system to internally overloaded. 9. Smurf Attack: Similar to a ping flood, a smurf strike depends on a large amount of ICMP echo request packages. But the similarity ends there, as a smurf attack applies an amplification course to boost their payload potential on broadcast networks. Smurf malware is used to produce this type of attack. 10. NTP Amplification: Internet-attached devices use NTP (network time protocol) servers for time synchronization. Resembling a DNS amplification attack, here a hacker uses a numerous of NTP servers to overload a victim with user datagram protocol (UDP) traffic.Preventing DoS Attack
The ultimate problem with these attacks is that you don't know when your system can be the target. You can minimize the possibility of being a part of such a strike, where your device can be used for illegal actions. Take note of the following advice on how to protect your devices from DoS attacks:- Install an antivirus program and firewall into your network if not already done. It helps in reducing the bandwidth usage to authenticated users only.
- Server configuration can increase the possibility of being attacked. If you’re a network administrator, take a look at network configurations and ensure the firewall policies to stop unauthenticated users from addressing the server’s resources.
- Certain third-party services provide guidance and protection against DoS attacks. Don't be unprepared for attack, use this solution for the safety of your IT system.

Preventing DDoS Attack
DDoS attacks, which attacks companies with vast amounts of traffic, freeze websites and switch essential services offline. 50% of DDoS attacks last between 6-24 hours, causing an estimated cost by $50,000 per hour. The number of DDoS attacks is increasing by 130% every year with a 40% jump in attack duration.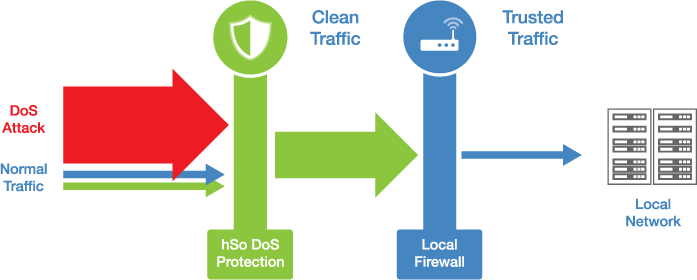
DDoS attacks target organizations no matter their size and individuals too. As fraudsters permanently try to develop more sophisticated DDoS methods, and each organization and persons that use the internet should learn how to minimize the dangers of a DDoS.
Here are 10 ways to be ready for eventually seriously DDoS attacks: 1. Provide Extra Bandwidth: First thing you need is to overprovision your bandwidth, that causes more time to determine and deal with a DDoS strike. It also provides your server to adapt to an unexpected situation in traffic, protecting you against the powerful attack. It won’t block a sizeable DDoS attack alone. Still, it could buy you crucial time before your resources became entirely overloaded. This method performs appropriately against volumetric DDoS attacks, and many companies use this system to increase bandwidth to absorb the enormous scopes of traffic. But, as the result of the race between scalable bandwidth and cyber-criminals, who came up with the solution for large companies that can afford that kind of expenses. 2. Resilient Architecture: If you want to endure the DDoS attack, it's necessary to make your architecture as strongest possible. Architecture priorities must be geographic and provider diverse. By developing your resources via multiple data centers, you will protect yourself, so if one service has knocked offline, you ensure your architecture with a backup. Proper cloud provider, like Microsoft Azure, will provide the right solution to host your services in geographically separate data centers, ensuring you with a backup if cyber-criminals attack you. 3. Action Plan: Your business should begin preparing to defend from DDoS attacks before you're stricken. It is more difficult to react after the strike is already in progress. While DDoS hits cannot be prevented, safety measures can be taken to make it more complicated for a perpetrator to knock you offline. DDoS attacks can hit at any time, so don’t just sit and wait. Make a system that can successfully defend you from DDoS attack. A DDoS action plan should contain use of automated reports to send an internal alert when your traffic runs beyond standards and registering your IT infrastructure to develop a network topology diagram with an asset inventory. 4. IoT Security: DDoS strikes are continually growing, and fraudsters now use large worldwide botnets comprised of IoT (Internet of Things) devices. The IoT, the global network of connected devices like smart TVs and refrigerators, is announced as the next industrial revolution. But, it is also the great news DDoS attackers. Because IoT devices are generally secure at a low-level and cyber-criminals are now able to leverage legions of attached devices to run traffic of their choosing target. Users and companies must increase the security of their devices, to minimize the power of DDoS attacks. One promptly and efficient method to do this is by updating from default factory-set passwords, hacked merely by fraudsters performing brute force techniques. Select a strong password and change it regularly. The best way to protect your device system is by choosing a strong and a long password. 5.Maintain Traffic Levels: DDoS create massive traffic spikes, but this could be unseen in real traffic. Wise hackers run DDoS attacks when websites and services are typically busy, on Christmas or Black Friday, and in that way, they camouflage the strike. The proper approach to identify a DDoS attack is to check out for unusual spikes in traffic to your website. Be careful, supervise traffic and set levels for automatic reports when these will be transcended.
6. CDN Usage: One of the weapons against a DDoS attack is a CDN (content delivery network). It functions by detecting traffic launched as a part of a DDoS strike and redirecting it to a third-party cloud infrastructure. The content delivery network isn't cheap, and a typical monthly plan can edge into the five zeros. It isn't the option for small companies. It’s a suitable solution for large organizations that can’t risk being knocked offline by a DDoS attack. Large establishments can invest in security continuously, and there's no end to the money they could spend. Some companies can’t afford CDN. Fortunately, it isn’t the only solution. 7. Simulation of Attacks: Simulation of DDoS attacks on your network can weigh how well your service works, as well as the performance level of your action plan. These artificial hits could operate as part of a penetration test, a safe hacking strike conducted by a capable, ethical hacker. These actions discover hidden security weaknesses and maintain how good companies or organizations could withstand DDoS hits. Anyway, you should be managing official penetration tests on your business to determine the security level. Launch a DDoS hit simulation during scheduled monitoring to spare your end clients the inconvenience, and if you have a CDN, you should inform the provider that it is a test. 8.Use a Dedicated Server: Buying a dedicated server means more bandwidth and better control over security. Opposite to co-location servers, dedicated servers' hardware and infrastructure will be conducted a third-party provider. Dedicated servers are also available with automatic DDoS attack mitigation in the case of a strike, and you will get support from your provider. 9.Customer Education: DDoS malware has hidden on numerous devices across the world. Cyber-criminal is a worldwide problem, and it is every businesses responsibility to develop security measures. Customer education is a crucial part of DDoS protection. DDoS strikers will be notably minimized if the number of educated users will rapidly grow. Dedicatedly protect your clients against cyber crooks by motivating them to keep track of security practices to guard their devices. 10.Staff Training: Knowledge is the tool, and you will require it to prevent and recover from a DDoS attack. Whoever is in charge for your IT infrastructure should comprehend proper incident handling procedure, so in the situation of a DDoS hit, they can react adequately and mitigate any further strikes. If your business is serious about withstanding and recovering from DDoS attacks, consider training a member of your staff in one of the plenty

